
Police will text 70,000 people to warn them they have been victims of a banking scam in the UK’s biggest anti-fraud operation.
The Metropolitan Police have arrested an east London man accused of running an international service enabling fake phone calls to victims.
Victims lost thousands of pounds, and in one case £3m.
Detectives only have their phone numbers and are asking people to act if they receive the message.
Metropolitan Police Commissioner Sir Mark Rowley described the investigation as the biggest proactive counter-fraud investigation ever in the UK.
He said the criminals involved were responsible for the “industrialisation of fraud”.
Detectives revealed that there could be 200,000 UK victims of the scams, which usually involved fraudsters calling, pretending to be a bank, warning a customer of alleged suspicious activity on their account.
An address in east London is alleged to have been at the centre of the service which police believe enabled fraud on a global scale.
How will people know the text is genuine?
During the investigation, police obtained the numbers of victims but not their names and addresses.
They will send a mass text message to 70,000 numbers asking people to go to the Action Fraud website to register their details.
Detectives are aware of the risks of using a text message to contact victims of fraud who may have been targeted through their mobile phones.
They said the message from the police would only have links to the Action Fraud site, and would only be sent on 24 and 25 November. Any other texts should be regarded as fraudulent themselves.
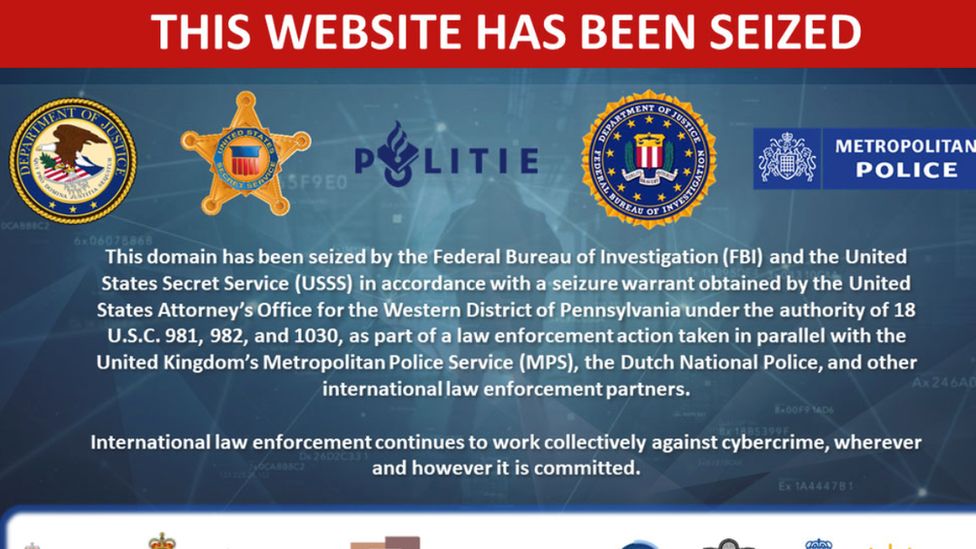
The iSpoof website, involved in the scam, was advertised openly on the internet. It allegedly provided access to a server, initially based in Holland and then Ukraine, which criminals could use to make anonymous calls to victims from a spoof phone number.
This allowed them to pose as employees of banks including Barclays, Santander, HSBC, Lloyds, Halifax, First Direct, NatWest, Nationwide and TSB.
Victims were asked to enter a “one-time code” or password for their account into their phone, which was intercepted by the iSpoof server and made available to the fraudsters.
Criminals could then use these details to “clear out the accounts” of their victims, detectives said.
‘Devastating crime’
Det Supt Helen Rance, from the Met’s Cyber Crime unit, said victims would not have known the phone call was coming from iSpoof.
“The person on the other end of the line can be very convincing,” she said.
“This is an absolutely devastating crime for so many people. They must be worried, I really feel for them,” she said.
Fraudsters paid between £150 and £5,000 a month in bitcoin to use the iSpoof service, contacting, at times, 20 people a minute, primarily in the USA, UK, Netherlands, Australia, France and Ireland.
So far, police believe £48m may have been stolen by criminals using iSpoof. This figure is likely to rise. Those behind the service are allegedly earning £3.2m and living “lavish” lifestyles.
A notice on the website says that it has been taken down by the FBI.
Det Supt Rance said the investigation remained live.

“We are still making arrests today and tomorrow,” she said. “This work will have prevented hundreds and thousands of online fraud crimes.
“Our message to criminals who have used this website is we have your details and are working hard to locate you, regardless of where you are.”
Operation Elaborate
Metropolitan Police fraud and cyber-crime detectives launched Operation Elaborate in June 2021 after asking experts which websites posed the greatest risk in the UK.
The Met said investigators infiltrated iSpoof and began gathering information, including 70 million data records.
A breakthrough came when they discovered that police in the Netherlands had placed a “bug”‘ on the server, allowing them to record calls being made through it.
This evidence was shared with police in the UK, and the European law enforcement bodies Europol and Eurojust.

Police believe 59,000 potential suspects may have used the iSpoof service, but are prioritising those in the UK who have spent at least 100 bitcoin to get access, believing they were anonymous.
Early in November 2022 they raided an address in east London and arrested a man alleged to be behind iSpoof.
In other raids, 120 people thought to have used the service for fraud have been taken into custody.
Det Supt Rance warned other criminal “enablers” will have taken over to provide services to fraudsters.
“Undoubtedly they will go to another website,” she said. “They have created back-ups. We have not solved this problem.”
But she said one major outcome of the investigation was to have “discredited” the iSpoof name.
A 34-year-old man, Teejai Fletcher, has been charged with making or supplying articles for use in fraud and participating in the activities of an organised crime group.
He will appear at Southwark Crown Court on 6 December.
Do you believe you’ve been scammed by fake callers? Have you received a notification of fraud from the police? Share your experiences by emailing haveyoursay@bbc.co.uk.
Please include a contact number if you are willing to speak to a BBC journalist. You can also get in touch in the following ways:
- WhatsApp: +44 7756 165803
- Tweet: @BBC_HaveYourSay
- Upload pictures or video
- Please read our terms & conditions and privacy policy
If you are reading this page and can’t see the form you will need to visit the mobile version of the BBC website to submit your question or comment or you can email us at HaveYourSay@bbc.co.uk. Please include your name, age and location with any submission.
